![]()
I got DHCPv6-PD aka prefix delegation up and running on a FortiGate. Yes! ✅ Configuring it is tricky since it’s not always clear, which options to use. You cannot see everything in the GUI (it even changes depending on other options made later on or selects hidden and wrong default values), hence you must set specific options via the CLI. I navigated around some bugs and finally got it running. Here we go:
Please refer to my previous blog post about DHCPv6 prefix delegation in detail.
Setup Notes
This is the basic lab, showing the ISP connection (green box, though not of interest for the following configs), as well as the Internet connection from the Forti (red box) and the internal clients (blue box):
![]()
- I’m using a FG-60F with FortiOS 7.6.1.
- The wan1 interface is attached to an AVM FRITZ!BOX 7560 with FRITZ!OS 07.30, acting as the DHCPv6 server for addresses (IA_NA) as well as for prefixes (IA_PD, handing out /62 prefixes).
- Have a look at RFC 8415 “Dynamic Host Configuration Protocol for IPv6 (DHCPv6)” respectively the IANA “Dynamic Host Configuration Protocol for IPv6 (DHCPv6)” for more details concerning the DHCPv6 option types.
- The internal interface shall use a /64 out of the delegated prefix.
- With FortiOS 7.4.6, the FortiGate did not succeed in requesting anything over DHCPv6 at all. I’ve no idea, why. Some notes here.
Eventually, I tried an upgrade to FortiOS 7.6.1, in which it worked. The same problem still exists with FortiOS 7.6.1. In the end, disabling/enabling the DHCPv6 client on the wan1 interface made it work.
- The FortiGate receives its default route through the RA from the Fritzbox. (Remember that DHCPv6 does NOT send a default route at all. Everyone must rely on RAs in any case!)
Though possible, I did not succeed in configuring the RA for the internal interface, serving a /64 out of the delegated range for the SLAAC method. Within the RA, the prefix did not show up at all. :( Most likely I forgot to set the IAPD value with “set delegated-prefix-iaid 5” within the “config ip6-delegated-prefix-list” section since I was able to get this running on some later scenarios.- Nevertheless, I configured the internal interface to send the RA with the M-flag while setting up a stateful DHCPv6 server on the FortiGate itself. With this option, I was able to hand out a /64 to the internal clients. ✅
- On several configuration options, you can choose a “subnet” which defaults to “::/0” in the GUI as well as in the CLI. This is like an identifier to set the n-th network within the delegated prefix. Always change this to something with a /64 (rather than the default /0) to get the job done correctly. Otherwise, the FortiGate chooses the full delegated prefix such as a /62 (rather than a /64) and uses it on its interface, which stands against any best practice, will kill SLAAC, makes me horribly sad, and so on.
- Within the configuration, you have to choose an “IAPD” value which defaults to 5. This value is randomly chosen by Fortinet and used later on to identify the delegated prefix. I left it by this value of 5. The ugly thing: You have to set this value for the stateful DHCPv6 server as well, but this cannot be done through the GUI. If you activate the DHCPv6 server with the “Delegated” IP mode, you’ll get an error in the GUI. That is: At least for this single entry you must use the CLI.
- At least in FortiOS 7.6.1 there is a bug in which the FortiGate does not reply to RSs with RAs. That is: Your clients won’t get the default route until the first RA that is sent on a regular basis by the Forti is received by those clients. As a workaround, I’ve set the min- and max-interval values to 10 respectively 30 seconds. Since the defaults are way higher (600 seconds = 10 minutes), clients have to wait really long until IPv6 is up and running.
- Another bug is related to the output of the routing table for IPv6, since it does not show the default route that is gathered from the RA on the wan1 interface. Funnily, this is only true for the
get router info6 routing-table but not for the
diagnose ipv6 route list output.
- Other quite useful information about FortiGate’s DHCPv6 configuration options can be found here and there.
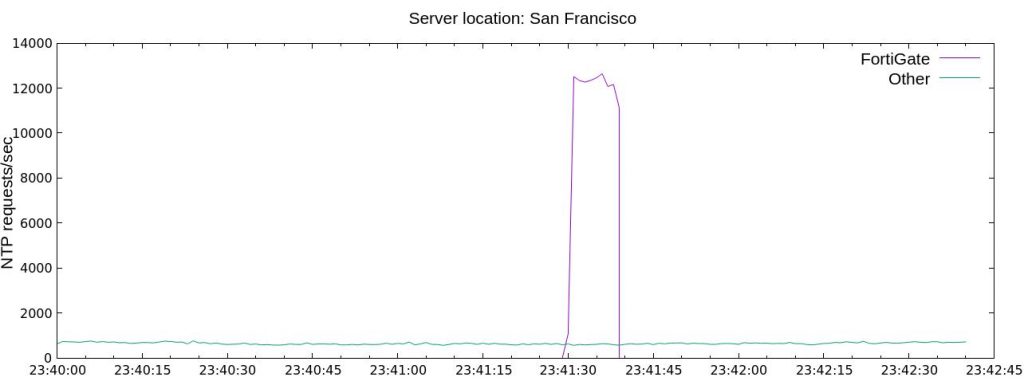
Configuration of the wan1 Interface
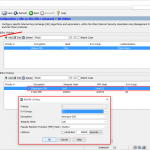
Through the GUI (kudos to Fortinet, in that we can now configure more IPv6 stuff through the GUI ;)). Note the “IAPD 5” without a prefix hint.
![]() CLI:
CLI:
config system interface
edit "wan1"
set vdom "root"
set mode dhcp
set allowaccess ping
config ipv6
set ip6-mode dhcp
set ip6-allowaccess ping
set dhcp6-prefix-delegation enable
config dhcp6-iapd-list
edit 5
next
end
end
next
end
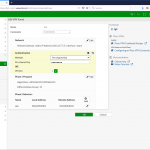
Configuration of the internal Interface
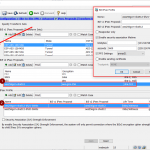
Basics are possible through the GUI, while you MUST set some values through the CLI later.
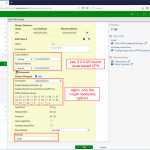
![]()
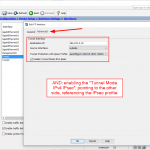
![]() Here is everything from the CLI in which you can set the “delegated-prefix-iaid 5” for the DHCPv6 server. Note that I changed the “ip6-other-flag” to disable since for stateful DHCPv6 you only need the M-flag:
Here is everything from the CLI in which you can set the “delegated-prefix-iaid 5” for the DHCPv6 server. Note that I changed the “ip6-other-flag” to disable since for stateful DHCPv6 you only need the M-flag:
config system interface
edit "internal"
set vdom "root"
config ipv6
set ip6-mode delegated
set ip6-allowaccess ping https ssh
set ip6-send-adv enable
set ip6-manage-flag enable
set ip6-other-flag disable
set ip6-max-interval 30
set ip6-min-interval 10
set ip6-delegated-prefix-iaid 5
set ip6-upstream-interface "wan1"
set ip6-subnet ::1/64
end
next
end
config system dhcp6 server
edit 1
set dns-service delegated
set subnet ::/64
set interface "internal"
set upstream-interface "wan1"
set delegated-prefix-iaid 5
set ip-mode delegated
next
end
Information
Some information can be gathered through the GUI and the CLI. Note the missing IPv6 default route in the GUI as well as in the first CLI command, while the second one lists the “gwy”:
![]()
![]()
![]()
FortiGate-60F # get router info6 routing-table
IPv6 Routing Table
Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF,
IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, B - BGP, V - BGP VPNv6
* - candidate default
Timers: Uptime
Routing table for VRF=0
C ::1/128 via ::, root, 00:19:47
C 2003:c6:af32:8400:6d5:90ff:fe42:8612/128 via ::, wan1, 00:07:38
C 2003:c6:af32:84fc::/64 via ::, internal, 00:03:47
FortiGate-60F #
FortiGate-60F #
FortiGate-60F #
FortiGate-60F # diagnose ipv6 route list
vf=0 vrf=0 tbl=65534 type=02(local) protocol=0(unspec) flag=80200000 prio=0 dst:::1/128 dev=18(root) pmtu=16436
vf=0 vrf=0 tbl=65534 type=02(local) protocol=0(unspec) flag=80200000 prio=0 dst:2003:c6:af32:8400:6d5:90ff:fe42:8612/128 dev=18(root) pmtu=16436
vf=0 vrf=0 tbl=65534 type=01(unicast) protocol=2(kernel) flag=00000000 prio=256 dst:2003:c6:af32:8400:6d5:90ff:fe42:8612/128 dev=5(wan1) pmtu=1492
vf=0 vrf=0 tbl=65534 type=02(local) protocol=0(unspec) flag=00300000 prio=0 dst:2003:c6:af32:84fc::/128 dev=18(root) pmtu=16436
vf=0 vrf=0 tbl=65534 type=02(local) protocol=0(unspec) flag=80200000 prio=0 dst:2003:c6:af32:84fc::1/128 dev=18(root) pmtu=16436
vf=0 vrf=0 tbl=65534 type=01(unicast) protocol=0(unspec) flag=01000200 prio=0 dst:2003:c6:af32:84fc::2/128 dev=23(internal) pmtu=1500
vf=0 vrf=0 tbl=65534 type=01(unicast) protocol=2(kernel) flag=00400000 prio=256 dst:2003:c6:af32:84fc::/64 dev=23(internal) pmtu=1500
vf=0 vrf=0 tbl=65534 type=02(local) protocol=0(unspec) flag=00300000 prio=0 dst:fe80::/128 dev=18(root) pmtu=16436
vf=0 vrf=0 tbl=65534 type=02(local) protocol=0(unspec) flag=00300000 prio=0 dst:fe80::/128 dev=18(root) pmtu=16436
[...]
vf=0 vrf=0 tbl=65534 type=01(unicast) protocol=3(boot) flag=00000000 prio=256 dst:ff00::/8 dev=5(wan1) pmtu=1492
vf=0 vrf=0 tbl=65534 type=01(unicast) protocol=3(boot) flag=00000000 prio=256 dst:ff00::/8 dev=6(wan2) pmtu=1500
vf=0 vrf=0 tbl=65534 type=01(unicast) protocol=2(kernel) flag=00450000 prio=1024 gwy:fe80::7eff:4dff:fe93:9b5 dev=5(wan1) pmtu=1492
vf=0 vrf=0 tbl=0 type=07(unreachable) protocol=2(kernel) flag=00200000 prio=-1 dev=18(root) pmtu=16436
FortiGate-60F #
![]()
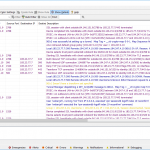
The following Wireshark screenshot shows the DHCPv6 messages between the FortiGate (wan1) and the Fritzbox. The first reply (message nr. 6) is one that wasn’t working correctly (status code 13 = no binding), for whatever reason. I disabled/enabled DHCPv6 on wan1 again. Messages 18-21 are the correct ones, handing out the /62 prefix:
![]()
This is the DHCPv6 debug log during the complete startup of the wan1 interface. Maybe someone finds hints about the mentioned DHCPv6 “no binding” issues:
=~=~=~=~=~=~=~=~=~=~=~= PuTTY log 2024.12.19 09:13:30 =~=~=~=~=~=~=~=~=~=~=~=
login as: admin
admin@192.168.1.99's password:
FortiGate-60F # diagnose debug reset
FortiGate-60F # diagnose debug console timestamp enable
FortiGate-60F # diagnose debug application dhcp6c 255
Debug messages will be on for 30 minutes.
FortiGate-60F # diagnose debug enable
FortiGate-60F # 2024-12-19 00:14:10 [debug]dhcp6_check_timer() called
2024-12-19 00:14:10 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:14:21 [debug]dhcp6_check_timer() called
2024-12-19 00:14:21 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:14:32 [debug]dhcp6_check_timer() called
2024-12-19 00:14:32 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:14:35 [info]dhcp6c_kernel_event_handler() dhcp6c_kernel_event_handler called
2024-12-19 00:14:35 [info]dhcp6c_intf_changed() intf changed. caller=0x92bae8
2024-12-19 00:14:35 [debug]dhcp6_check_timer() called
2024-12-19 00:14:35 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:36 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:14:36 [debug]dhcp6_check_timer() called
2024-12-19 00:14:36 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:36 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:14:36 [debug]dhcp6_check_timer() called
2024-12-19 00:14:36 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:14:36 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:14:36 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:14:36 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:14:36 [debug]dhcp6_check_timer() called
2024-12-19 00:14:36 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:14:36 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:14:36 [debug]dhcp6_check_timer() called
2024-12-19 00:14:36 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:14:37 [info]dhcp6c_kernel_event_handler() dhcp6c_kernel_event_handler called
2024-12-19 00:14:37 [info]dhcp6c_intf_changed() intf changed. caller=0x92bae8
2024-12-19 00:14:37 [debug]dhcp6_check_timer() called
2024-12-19 00:14:37 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:39 [info]dhcp6c_kernel_event_handler() dhcp6c_kernel_event_handler called
2024-12-19 00:14:39 [info]dhcp6c_intf_changed() intf changed. caller=0x92bae8
2024-12-19 00:14:39 [debug]dhcp6_check_timer() called
2024-12-19 00:14:39 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:40 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:14:40 [info]dhcp6c_nlm_handler() Restart and renew interface wan1.
2024-12-19 00:14:40 [debug]dhcp6_remove_event() removing an event on wan1, state=SOLICIT
2024-12-19 00:14:40 [warning]uncache_intf6_info() delete interface wan1 cache
2024-12-19 00:14:40 [debug]dhcp6c_intf_get_duid() called
2024-12-19 00:14:40 [debug]dhcp6c_intf_get_duid() Generated a new DUID: 00:03:00:01:04:d5:90:42:86:12.
2024-12-19 00:14:40 [debug]dhcp6_reset_timer() reset a timer on wan1, state=INIT, timeo=0, retrans=76
2024-12-19 00:14:40 [info]dhcp6c_nlm_handler() Restart and renew interface wan1.
2024-12-19 00:14:40 [debug]dhcp6_remove_event() removing an event on wan1, state=INIT
2024-12-19 00:14:40 [warning]uncache_intf6_info() delete interface wan1 cache
2024-12-19 00:14:40 [debug]dhcp6c_intf_get_duid() called
2024-12-19 00:14:40 [debug]dhcp6c_intf_get_duid() Generated a new DUID: 00:03:00:01:04:d5:90:42:86:12.
2024-12-19 00:14:40 [debug]dhcp6_reset_timer() reset a timer on wan1, state=INIT, timeo=0, retrans=188
2024-12-19 00:14:40 [info]dhcp6c_nlm_handler() Restart and renew interface wan1.
2024-12-19 00:14:40 [debug]dhcp6_remove_event() removing an event on wan1, state=INIT
2024-12-19 00:14:40 [warning]uncache_intf6_info() delete interface wan1 cache
2024-12-19 00:14:40 [debug]dhcp6c_intf_get_duid() called
2024-12-19 00:14:40 [debug]dhcp6c_intf_get_duid() Generated a new DUID: 00:03:00:01:04:d5:90:42:86:12.
2024-12-19 00:14:40 [debug]dhcp6_reset_timer() reset a timer on wan1, state=INIT, timeo=0, retrans=561
2024-12-19 00:14:40 [debug]dhcp6_check_timer() called
2024-12-19 00:14:40 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:40 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:14:40 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:14:40 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:14:40 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:14:40 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:14:40 [debug]dhcp6_check_timer() called
2024-12-19 00:14:40 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:40 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:14:40 [debug]dhcp6_check_timer() called
2024-12-19 00:14:40 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:43 [debug]dhcp6_check_timer() called
2024-12-19 00:14:43 [debug]dhcp6_check_timer() timer func=0x9274f0
2024-12-19 00:14:43 [debug]client6_send() a new XID (503090) is generated
2024-12-19 00:14:43 [debug]copy_option() set client ID (len 10)
2024-12-19 00:14:43 [debug]copyout_option() set identity association
2024-12-19 00:14:43 [debug]copy_option() set elapsed time (len 2)
2024-12-19 00:14:43 [debug]copy_option() set option request (len 4)
2024-12-19 00:14:43 [debug]copyout_option() set IA_PD
2024-12-19 00:14:43 [debug]client6_send() send solicit to ff02::1:2%wan1
2024-12-19 00:14:43 [debug]dhcp6_reset_timer() reset a timer on wan1, state=SOLICIT, timeo=0, retrans=1049
2024-12-19 00:14:43 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:14:43 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:14:43 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:14:43 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:14:43 [debug]dhcp6_check_timer() called
2024-12-19 00:14:43 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:43 [info]client6_mainloop() msg received, sock =11
2024-12-19 00:14:43 [debug]client6_recv() receive advertise from fe80::7eff:4dff:fe93:9b5%wan1 on wan1
2024-12-19 00:14:43 [debug]dhcp6_get_options() get DHCP option client ID, len 10
2024-12-19 00:14:43 [debug] DUID: 00:03:00:01:04:d5:90:42:86:12
2024-12-19 00:14:43 [debug]dhcp6_get_options() get DHCP option server ID, len 10
2024-12-19 00:14:43 [debug] DUID: 00:03:00:01:7c:ff:4d:93:09:b5
2024-12-19 00:14:43 [debug]dhcp6_get_options() get DHCP option preference, len 1
2024-12-19 00:14:43 [debug] preference: 0
2024-12-19 00:14:43 [debug]dhcp6_get_options() get DHCP option DNS, len 16
2024-12-19 00:14:43 [debug]dhcp6_get_options() get DHCP option opt_86, len 16
2024-12-19 00:14:43 [info]dhcp6_get_options() unknown or unexpected DHCP6 option opt_86, len 16
2024-12-19 00:14:43 [debug]dhcp6_get_options() get DHCP option identity association, len 40
2024-12-19 00:14:43 [debug] IA_NA: ID=5, T1=1800, T2=2880
2024-12-19 00:14:43 [debug]copyin_option() get DHCP option IA address, len 24
2024-12-19 00:14:43 [debug]copyin_option() IA_NA address: 2003:c6:af32:8400:6d5:90ff:fe42:8612 pltime=3600 vltime=7200
2024-12-19 00:14:43 [debug]dhcp6_get_options() get DHCP option IA_PD, len 41
2024-12-19 00:14:43 [debug] IA_PD: ID=5, T1=1800, T2=2880
2024-12-19 00:14:43 [debug]copyin_option() get DHCP option IA_PD prefix, len 25
2024-12-19 00:14:43 [debug]copyin_option() IA_PD prefix: 2003:c6:af32:84fc::/62 pltime=3600 vltime=7200
2024-12-19 00:14:43 [debug]client6_recvadvert() server ID: 00:03:00:01:7c:ff:4d:93:09:b5, pref=0
2024-12-19 00:14:43 [debug]client6_recvadvert() reset timer for wan1 to 0.990649
2024-12-19 00:14:43 [debug]dhcp6_check_timer() called
2024-12-19 00:14:43 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:45 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:14:45 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:14:45 [debug]dhcp6_check_timer() called
2024-12-19 00:14:45 [debug]dhcp6_check_timer() timer func=0x9274f0
2024-12-19 00:14:45 [debug]select_server() picked a server (ID: 00:03:00:01:7c:ff:4d:93:09:b5)
2024-12-19 00:14:45 [debug]client6_send() a new XID (1cf373) is generated
2024-12-19 00:14:45 [debug]copy_option() set client ID (len 10)
2024-12-19 00:14:45 [debug]copy_option() set server ID (len 10)
2024-12-19 00:14:45 [debug]copyout_option() set IA address
2024-12-19 00:14:45 [debug]copyout_option() set identity association
2024-12-19 00:14:45 [debug]copy_option() set elapsed time (len 2)
2024-12-19 00:14:45 [debug]copy_option() set option request (len 4)
2024-12-19 00:14:45 [debug]copyout_option() set IA_PD prefix
2024-12-19 00:14:45 [debug]copyout_option() set IA_PD
2024-12-19 00:14:45 [debug]client6_send() send request to ff02::1:2%wan1
2024-12-19 00:14:45 [debug]dhcp6_reset_timer() reset a timer on wan1, state=REQUEST, timeo=0, retrans=1080
2024-12-19 00:14:45 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:45 [info]client6_mainloop() msg received, sock =11
2024-12-19 00:14:45 [debug]client6_recv() receive reply from fe80::7eff:4dff:fe93:9b5%wan1 on wan1
2024-12-19 00:14:45 [debug]dhcp6_get_options() get DHCP option client ID, len 10
2024-12-19 00:14:45 [debug] DUID: 00:03:00:01:04:d5:90:42:86:12
2024-12-19 00:14:45 [debug]dhcp6_get_options() get DHCP option server ID, len 10
2024-12-19 00:14:45 [debug] DUID: 00:03:00:01:7c:ff:4d:93:09:b5
2024-12-19 00:14:45 [debug]dhcp6_get_options() get DHCP option status code, len 16
2024-12-19 00:14:45 [debug] status code: no binding
2024-12-19 00:14:45 [info]client6_recvreply() status code: no binding
2024-12-19 00:14:45 [debug]dhcp6c_ha_sync_send_lease_to() [dhcp6c_ha_sync_send_lease_to] serialno=' (null)', intf='wan1'
2024-12-19 00:14:45 [debug]dhcp6c_ha_sync_send_lease_to() send DHCP6_HA_SYNC_T_LEASE
2024-12-19 00:14:45 [debug]dhcp6_remove_event() removing an event on wan1, state=REQUEST
2024-12-19 00:14:45 [debug]dhcp6_remove_event() removing server (ID: 00:03:00:01:7c:ff:4d:93:09:b5)
2024-12-19 00:14:45 [debug]client6_recvreply() got an expected reply, sleeping.
2024-12-19 00:14:45 [debug]dhcp6_check_timer() called
2024-12-19 00:14:45 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:48 [debug]dhcp6_check_timer() called
2024-12-19 00:14:48 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:14:48 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:14:48 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:14:48 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:14:48 [debug]dhcp6_check_timer() called
2024-12-19 00:14:48 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:50 [debug]dhcp6_check_timer() called
2024-12-19 00:14:50 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:52 [debug]dhcp6_check_timer() called
2024-12-19 00:14:52 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:54 [debug]dhcp6_check_timer() called
2024-12-19 00:14:54 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:56 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:14:56 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:14:56 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:14:56 [debug]dhcp6_check_timer() called
2024-12-19 00:14:56 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:14:59 [debug]dhcp6_check_timer() called
2024-12-19 00:14:59 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:14:59 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:14:59 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:14:59 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:14:59 [debug]dhcp6_check_timer() called
2024-12-19 00:14:59 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:01 [debug]dhcp6_check_timer() called
2024-12-19 00:15:01 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:03 [debug]dhcp6_check_timer() called
2024-12-19 00:15:03 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:05 [debug]dhcp6_check_timer() called
2024-12-19 00:15:05 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:07 [debug]dhcp6_check_timer() called
2024-12-19 00:15:07 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:09 [debug]dhcp6_check_timer() called
2024-12-19 00:15:09 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:11 [debug]dhcp6_check_timer() called
2024-12-19 00:15:11 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:13 [debug]dhcp6_check_timer() called
2024-12-19 00:15:13 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:15 [debug]dhcp6_check_timer() called
2024-12-19 00:15:15 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:17 [debug]dhcp6_check_timer() called
2024-12-19 00:15:17 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:19 [debug]dhcp6_check_timer() called
2024-12-19 00:15:19 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:21 [debug]dhcp6_check_timer() called
2024-12-19 00:15:21 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:23 [debug]dhcp6_check_timer() called
2024-12-19 00:15:23 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:25 [debug]dhcp6_check_timer() called
2024-12-19 00:15:25 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:26 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:15:26 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:15:26 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:15:26 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:15:26 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:15:26 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:15:26 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:15:26 [debug]dhcp6_check_timer() called
2024-12-19 00:15:26 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:29 [debug]dhcp6_check_timer() called
2024-12-19 00:15:29 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:15:29 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:15:29 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:15:29 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:15:29 [debug]dhcp6_check_timer() called
2024-12-19 00:15:29 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:29 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:15:29 [debug]dhcp6_check_timer() called
2024-12-19 00:15:29 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:31 [debug]dhcp6_check_timer() called
2024-12-19 00:15:31 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:33 [debug]dhcp6_check_timer() called
2024-12-19 00:15:33 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:35 [debug]dhcp6_check_timer() called
2024-12-19 00:15:35 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:37 [debug]dhcp6_check_timer() called
2024-12-19 00:15:37 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:39 [debug]dhcp6_check_timer() called
2024-12-19 00:15:39 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:41 [debug]dhcp6_check_timer() called
2024-12-19 00:15:41 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:43 [debug]dhcp6_check_timer() called
2024-12-19 00:15:43 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:45 [debug]dhcp6_check_timer() called
2024-12-19 00:15:45 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:47 [debug]dhcp6_check_timer() called
2024-12-19 00:15:47 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:49 [debug]dhcp6_check_timer() called
2024-12-19 00:15:49 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:51 [debug]dhcp6_check_timer() called
2024-12-19 00:15:51 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:53 [debug]dhcp6_check_timer() called
2024-12-19 00:15:53 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:55 [debug]dhcp6_check_timer() called
2024-12-19 00:15:55 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:57 [debug]dhcp6_check_timer() called
2024-12-19 00:15:57 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:15:59 [debug]dhcp6_check_timer() called
2024-12-19 00:15:59 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:01 [debug]dhcp6_check_timer() called
2024-12-19 00:16:01 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:03 [debug]dhcp6_check_timer() called
2024-12-19 00:16:03 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:05 [debug]dhcp6_check_timer() called
2024-12-19 00:16:05 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:07 [debug]dhcp6_check_timer() called
2024-12-19 00:16:07 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:09 [debug]dhcp6_check_timer() called
2024-12-19 00:16:09 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:11 [debug]dhcp6_check_timer() called
2024-12-19 00:16:11 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:14 [debug]dhcp6_check_timer() called
2024-12-19 00:16:14 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:16 [debug]dhcp6_check_timer() called
2024-12-19 00:16:16 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:18 [debug]dhcp6_check_timer() called
2024-12-19 00:16:18 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:20 [debug]dhcp6_check_timer() called
2024-12-19 00:16:20 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:22 [debug]dhcp6_check_timer() called
2024-12-19 00:16:22 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:24 [debug]dhcp6_check_timer() called
2024-12-19 00:16:24 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:26 [debug]dhcp6_check_timer() called
2024-12-19 00:16:26 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:26 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:16:26 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:16:26 [debug]dhcp6_check_timer() called
2024-12-19 00:16:26 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:29 [debug]dhcp6_check_timer() called
2024-12-19 00:16:29 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:16:29 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:16:29 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:16:29 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:16:29 [debug]dhcp6_check_timer() called
2024-12-19 00:16:29 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:31 [debug]dhcp6_check_timer() called
2024-12-19 00:16:31 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:33 [debug]dhcp6_check_timer() called
2024-12-19 00:16:33 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:35 [debug]dhcp6_check_timer() called
2024-12-19 00:16:35 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:37 [debug]dhcp6_check_timer() called
2024-12-19 00:16:37 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:39 [debug]dhcp6_check_timer() called
2024-12-19 00:16:39 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:41 [debug]dhcp6_check_timer() called
2024-12-19 00:16:41 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:43 [debug]dhcp6_check_timer() called
2024-12-19 00:16:43 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:45 [debug]dhcp6_check_timer() called
2024-12-19 00:16:45 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:47 [debug]dhcp6_check_timer() called
2024-12-19 00:16:47 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:49 [debug]dhcp6_check_timer() called
2024-12-19 00:16:49 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:51 [debug]dhcp6_check_timer() called
2024-12-19 00:16:51 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:53 [debug]dhcp6_check_timer() called
2024-12-19 00:16:53 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:53 [debug]dhcp6_check_timer() called
2024-12-19 00:16:53 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:55 [debug]dhcp6_check_timer() called
2024-12-19 00:16:55 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:55 [debug]dhcp6_check_timer() called
2024-12-19 00:16:55 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:16:57 [debug]dhcp6_check_timer() called
2024-12-19 00:16:57 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:00 [debug]dhcp6_check_timer() called
2024-12-19 00:17:00 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:00 [debug]dhcp6_check_timer() called
2024-12-19 00:17:00 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:02 [debug]dhcp6_check_timer() called
2024-12-19 00:17:02 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:04 [debug]dhcp6_check_timer() called
2024-12-19 00:17:04 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:07 [info]dhcp6c_intf_changed() intf changed. caller=0x9273d0
2024-12-19 00:17:07 [debug]dhcp6_check_timer() called
2024-12-19 00:17:07 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:07 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:17:07 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:17:07 [debug]dhcp6_check_timer() called
2024-12-19 00:17:07 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:10 [debug]dhcp6_check_timer() called
2024-12-19 00:17:10 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:17:10 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:17:10 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:17:10 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:17:10 [debug]interface_has_changed() new dhcp6c options detected
2024-12-19 00:17:10 [debug]dhcp6c_resource_update() dhcp6client: detected changed interface, reinterfaceuring
2024-12-19 00:17:10 [warning]uncache_intf6_info() delete interface wan1 cache
2024-12-19 00:17:10 [debug]dhcp6c_intf_get_duid() called
2024-12-19 00:17:10 [debug]dhcp6c_intf_get_duid() Generated a new DUID: 00:03:00:01:04:d5:90:42:86:12.
2024-12-19 00:17:10 [debug]dhcp6_reset_timer() reset a timer on wan1, state=INIT, timeo=0, retrans=459
2024-12-19 00:17:10 [debug]dhcp6_check_timer() called
2024-12-19 00:17:10 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:12 [debug]dhcp6_check_timer() called
2024-12-19 00:17:12 [debug]dhcp6_check_timer() timer func=0x9274f0
2024-12-19 00:17:12 [debug]client6_send() a new XID (b4c06e) is generated
2024-12-19 00:17:12 [debug]copy_option() set client ID (len 10)
2024-12-19 00:17:12 [debug]copy_option() set elapsed time (len 2)
2024-12-19 00:17:12 [debug]copy_option() set option request (len 4)
2024-12-19 00:17:12 [debug]copyout_option() set IA_PD
2024-12-19 00:17:12 [debug]client6_send() send solicit to ff02::1:2%wan1
2024-12-19 00:17:12 [debug]dhcp6_reset_timer() reset a timer on wan1, state=SOLICIT, timeo=0, retrans=1046
2024-12-19 00:17:12 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:12 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:12 [debug]dhcp6_check_timer() called
2024-12-19 00:17:12 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:12 [info]client6_mainloop() msg received, sock =11
2024-12-19 00:17:12 [debug]client6_recv() receive advertise from fe80::7eff:4dff:fe93:9b5%wan1 on wan1
2024-12-19 00:17:12 [debug]dhcp6_get_options() get DHCP option client ID, len 10
2024-12-19 00:17:12 [debug] DUID: 00:03:00:01:04:d5:90:42:86:12
2024-12-19 00:17:12 [debug]dhcp6_get_options() get DHCP option server ID, len 10
2024-12-19 00:17:12 [debug] DUID: 00:03:00:01:7c:ff:4d:93:09:b5
2024-12-19 00:17:12 [debug]dhcp6_get_options() get DHCP option preference, len 1
2024-12-19 00:17:12 [debug] preference: 0
2024-12-19 00:17:12 [debug]dhcp6_get_options() get DHCP option DNS, len 16
2024-12-19 00:17:12 [debug]dhcp6_get_options() get DHCP option opt_86, len 16
2024-12-19 00:17:12 [info]dhcp6_get_options() unknown or unexpected DHCP6 option opt_86, len 16
2024-12-19 00:17:12 [debug]dhcp6_get_options() get DHCP option IA_PD, len 41
2024-12-19 00:17:12 [debug] IA_PD: ID=5, T1=1800, T2=2880
2024-12-19 00:17:12 [debug]copyin_option() get DHCP option IA_PD prefix, len 25
2024-12-19 00:17:12 [debug]copyin_option() IA_PD prefix: 2003:c6:af32:84fc::/62 pltime=3600 vltime=7200
2024-12-19 00:17:12 [debug]client6_recvadvert() server ID: 00:03:00:01:7c:ff:4d:93:09:b5, pref=0
2024-12-19 00:17:12 [debug]client6_recvadvert() reset timer for wan1 to 0.991872
2024-12-19 00:17:12 [debug]dhcp6_check_timer() called
2024-12-19 00:17:12 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:14 [info]dhcp6c_intf_changed() intf changed. caller=0x9273d0
2024-12-19 00:17:14 [debug]dhcp6_check_timer() called
2024-12-19 00:17:14 [debug]dhcp6_check_timer() timer func=0x9274f0
2024-12-19 00:17:14 [debug]select_server() picked a server (ID: 00:03:00:01:7c:ff:4d:93:09:b5)
2024-12-19 00:17:14 [debug]client6_send() a new XID (f583c6) is generated
2024-12-19 00:17:14 [debug]copy_option() set client ID (len 10)
2024-12-19 00:17:14 [debug]copy_option() set server ID (len 10)
2024-12-19 00:17:14 [debug]copy_option() set elapsed time (len 2)
2024-12-19 00:17:14 [debug]copy_option() set option request (len 4)
2024-12-19 00:17:14 [debug]copyout_option() set IA_PD prefix
2024-12-19 00:17:14 [debug]copyout_option() set IA_PD
2024-12-19 00:17:14 [debug]client6_send() send request to ff02::1:2%wan1
2024-12-19 00:17:14 [debug]dhcp6_reset_timer() reset a timer on wan1, state=REQUEST, timeo=0, retrans=949
2024-12-19 00:17:14 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:14 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:17:14 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:17:14 [debug]dhcp6_check_timer() called
2024-12-19 00:17:14 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:14 [info]client6_mainloop() msg received, sock =11
2024-12-19 00:17:14 [debug]client6_recv() receive reply from fe80::7eff:4dff:fe93:9b5%wan1 on wan1
2024-12-19 00:17:14 [debug]dhcp6_get_options() get DHCP option client ID, len 10
2024-12-19 00:17:14 [debug] DUID: 00:03:00:01:04:d5:90:42:86:12
2024-12-19 00:17:14 [debug]dhcp6_get_options() get DHCP option server ID, len 10
2024-12-19 00:17:14 [debug] DUID: 00:03:00:01:7c:ff:4d:93:09:b5
2024-12-19 00:17:14 [debug]dhcp6_get_options() get DHCP option preference, len 1
2024-12-19 00:17:14 [debug] preference: 0
2024-12-19 00:17:14 [debug]dhcp6_get_options() get DHCP option DNS, len 16
2024-12-19 00:17:14 [debug]dhcp6_get_options() get DHCP option opt_86, len 16
2024-12-19 00:17:14 [info]dhcp6_get_options() unknown or unexpected DHCP6 option opt_86, len 16
2024-12-19 00:17:14 [debug]dhcp6_get_options() get DHCP option IA_PD, len 41
2024-12-19 00:17:14 [debug] IA_PD: ID=5, T1=1800, T2=2880
2024-12-19 00:17:14 [debug]copyin_option() get DHCP option IA_PD prefix, len 25
2024-12-19 00:17:14 [debug]copyin_option() IA_PD prefix: 2003:c6:af32:84fc::/62 pltime=3600 vltime=7200
2024-12-19 00:17:14 [debug]info_printf() nameserver[0] 2620:fe::fe
2024-12-19 00:17:14 [debug]client6_process() dynamic dns1=[2620:fe::fe]
2024-12-19 00:17:14 [debug]get_ia() make an IA: PD-5
2024-12-19 00:17:14 [debug]update_prefix() create a prefix 2003:c6:af32:84fc::/62 pltime=3600, vltime=7200
2024-12-19 00:17:14 [debug]dhcp6c_ha_sync_send_lease_to() [dhcp6c_ha_sync_send_lease_to] serialno=' (null)', intf='wan1'
2024-12-19 00:17:14 [debug]dhcp6c_ha_sync_send_lease_to() send DHCP6_HA_SYNC_T_LEASE
2024-12-19 00:17:14 [debug]dhcp6_remove_event() removing an event on wan1, state=REQUEST
2024-12-19 00:17:14 [debug]dhcp6_remove_event() removing server (ID: 00:03:00:01:7c:ff:4d:93:09:b5)
2024-12-19 00:17:14 [debug]client6_recvreply() got an expected reply, sleeping.
2024-12-19 00:17:14 [debug]dhcp6_check_timer() called
2024-12-19 00:17:14 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:14 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:14 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:17:14 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:17:14 [debug]dhcp6_check_timer() called
2024-12-19 00:17:14 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:14 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:17:14 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:17:14 [debug]dhcp6_check_timer() called
2024-12-19 00:17:14 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:14 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:14 [debug]dhcp6_check_timer() called
2024-12-19 00:17:14 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:14 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:14 [info]dhcp6c_nlm_handler() Restart and renew interface wan1.
2024-12-19 00:17:14 [debug]remove_ia() remove an IA: PD-5
2024-12-19 00:17:14 [debug]remove_siteprefix() remove a site prefix 2003:c6:af32:84fc::/62
2024-12-19 00:17:14 [warning]uncache_intf6_info() delete interface wan1 cache
2024-12-19 00:17:14 [debug]dhcp6c_intf_get_duid() called
2024-12-19 00:17:14 [debug]dhcp6c_intf_get_duid() Generated a new DUID: 00:03:00:01:04:d5:90:42:86:12.
2024-12-19 00:17:14 [debug]dhcp6_reset_timer() reset a timer on wan1, state=INIT, timeo=0, retrans=601
2024-12-19 00:17:14 [info]dhcp6c_nlm_handler() Restart and renew interface wan1.
2024-12-19 00:17:14 [debug]dhcp6_remove_event() removing an event on wan1, state=INIT
2024-12-19 00:17:14 [warning]uncache_intf6_info() delete interface wan1 cache
2024-12-19 00:17:14 [debug]dhcp6c_intf_get_duid() called
2024-12-19 00:17:14 [debug]dhcp6c_intf_get_duid() Generated a new DUID: 00:03:00:01:04:d5:90:42:86:12.
2024-12-19 00:17:14 [debug]dhcp6_reset_timer() reset a timer on wan1, state=INIT, timeo=0, retrans=749
2024-12-19 00:17:14 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:14 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:14 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:14 [debug]dhcp6_check_timer() called
2024-12-19 00:17:14 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:14 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:17:14 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:17:14 [debug]dhcp6_check_timer() called
2024-12-19 00:17:14 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:16 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:16 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:16 [debug]dhcp6_check_timer() called
2024-12-19 00:17:16 [debug]dhcp6_check_timer() timer func=0x9274f0
2024-12-19 00:17:16 [debug]client6_send() a new XID (620a9f) is generated
2024-12-19 00:17:16 [debug]copy_option() set client ID (len 10)
2024-12-19 00:17:16 [debug]copyout_option() set identity association
2024-12-19 00:17:16 [debug]copy_option() set elapsed time (len 2)
2024-12-19 00:17:16 [debug]copy_option() set option request (len 4)
2024-12-19 00:17:16 [debug]copyout_option() set IA_PD
2024-12-19 00:17:16 [debug]client6_send() send solicit to ff02::1:2%wan1
2024-12-19 00:17:16 [debug]dhcp6_reset_timer() reset a timer on wan1, state=SOLICIT, timeo=0, retrans=1085
2024-12-19 00:17:16 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:16 [info]client6_mainloop() msg received, sock =11
2024-12-19 00:17:16 [debug]client6_recv() receive advertise from fe80::7eff:4dff:fe93:9b5%wan1 on wan1
2024-12-19 00:17:16 [debug]dhcp6_get_options() get DHCP option client ID, len 10
2024-12-19 00:17:16 [debug] DUID: 00:03:00:01:04:d5:90:42:86:12
2024-12-19 00:17:16 [debug]dhcp6_get_options() get DHCP option server ID, len 10
2024-12-19 00:17:16 [debug] DUID: 00:03:00:01:7c:ff:4d:93:09:b5
2024-12-19 00:17:16 [debug]dhcp6_get_options() get DHCP option preference, len 1
2024-12-19 00:17:16 [debug] preference: 0
2024-12-19 00:17:16 [debug]dhcp6_get_options() get DHCP option DNS, len 16
2024-12-19 00:17:16 [debug]dhcp6_get_options() get DHCP option opt_86, len 16
2024-12-19 00:17:16 [info]dhcp6_get_options() unknown or unexpected DHCP6 option opt_86, len 16
2024-12-19 00:17:16 [debug]dhcp6_get_options() get DHCP option identity association, len 40
2024-12-19 00:17:16 [debug] IA_NA: ID=5, T1=1800, T2=2880
2024-12-19 00:17:16 [debug]copyin_option() get DHCP option IA address, len 24
2024-12-19 00:17:16 [debug]copyin_option() IA_NA address: 2003:c6:af32:8400:6d5:90ff:fe42:8612 pltime=3600 vltime=7200
2024-12-19 00:17:16 [debug]dhcp6_get_options() get DHCP option IA_PD, len 41
2024-12-19 00:17:16 [debug] IA_PD: ID=5, T1=1800, T2=2880
2024-12-19 00:17:16 [debug]copyin_option() get DHCP option IA_PD prefix, len 25
2024-12-19 00:17:16 [debug]copyin_option() IA_PD prefix: 2003:c6:af32:84fc::/62 pltime=3600 vltime=7200
2024-12-19 00:17:16 [debug]client6_recvadvert() server ID: 00:03:00:01:7c:ff:4d:93:09:b5, pref=0
2024-12-19 00:17:16 [debug]client6_recvadvert() reset timer for wan1 to 0.988651
2024-12-19 00:17:16 [debug]dhcp6_check_timer() called
2024-12-19 00:17:16 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:19 [debug]dhcp6_check_timer() called
2024-12-19 00:17:19 [debug]dhcp6_check_timer() timer func=0x9274f0
2024-12-19 00:17:19 [debug]select_server() picked a server (ID: 00:03:00:01:7c:ff:4d:93:09:b5)
2024-12-19 00:17:19 [debug]client6_send() a new XID (ad2c8a) is generated
2024-12-19 00:17:19 [debug]copy_option() set client ID (len 10)
2024-12-19 00:17:19 [debug]copy_option() set server ID (len 10)
2024-12-19 00:17:19 [debug]copyout_option() set IA address
2024-12-19 00:17:19 [debug]copyout_option() set identity association
2024-12-19 00:17:19 [debug]copy_option() set elapsed time (len 2)
2024-12-19 00:17:19 [debug]copy_option() set option request (len 4)
2024-12-19 00:17:19 [debug]copyout_option() set IA_PD prefix
2024-12-19 00:17:19 [debug]copyout_option() set IA_PD
2024-12-19 00:17:19 [debug]client6_send() send request to ff02::1:2%wan1
2024-12-19 00:17:19 [debug]dhcp6_reset_timer() reset a timer on wan1, state=REQUEST, timeo=0, retrans=1022
2024-12-19 00:17:19 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:17:19 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:17:19 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:17:19 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:17:19 [debug]dhcp6_check_timer() called
2024-12-19 00:17:19 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:19 [info]client6_mainloop() msg received, sock =11
2024-12-19 00:17:19 [debug]client6_recv() receive reply from fe80::7eff:4dff:fe93:9b5%wan1 on wan1
2024-12-19 00:17:19 [debug]dhcp6_get_options() get DHCP option client ID, len 10
2024-12-19 00:17:19 [debug] DUID: 00:03:00:01:04:d5:90:42:86:12
2024-12-19 00:17:19 [debug]dhcp6_get_options() get DHCP option server ID, len 10
2024-12-19 00:17:19 [debug] DUID: 00:03:00:01:7c:ff:4d:93:09:b5
2024-12-19 00:17:19 [debug]dhcp6_get_options() get DHCP option preference, len 1
2024-12-19 00:17:19 [debug] preference: 0
2024-12-19 00:17:19 [debug]dhcp6_get_options() get DHCP option DNS, len 16
2024-12-19 00:17:19 [debug]dhcp6_get_options() get DHCP option opt_86, len 16
2024-12-19 00:17:19 [info]dhcp6_get_options() unknown or unexpected DHCP6 option opt_86, len 16
2024-12-19 00:17:19 [debug]dhcp6_get_options() get DHCP option identity association, len 40
2024-12-19 00:17:19 [debug] IA_NA: ID=5, T1=1800, T2=2880
2024-12-19 00:17:19 [debug]copyin_option() get DHCP option IA address, len 24
2024-12-19 00:17:19 [debug]copyin_option() IA_NA address: 2003:c6:af32:8400:6d5:90ff:fe42:8612 pltime=3600 vltime=7200
2024-12-19 00:17:19 [debug]dhcp6_get_options() get DHCP option IA_PD, len 41
2024-12-19 00:17:19 [debug] IA_PD: ID=5, T1=1800, T2=2880
2024-12-19 00:17:19 [debug]copyin_option() get DHCP option IA_PD prefix, len 25
2024-12-19 00:17:19 [debug]copyin_option() IA_PD prefix: 2003:c6:af32:84fc::/62 pltime=3600 vltime=7200
2024-12-19 00:17:19 [debug]info_printf() nameserver[0] 2620:fe::fe
2024-12-19 00:17:19 [debug]client6_process() dynamic dns1=[2620:fe::fe]
2024-12-19 00:17:19 [debug]get_ia() make an IA: PD-5
2024-12-19 00:17:19 [debug]update_prefix() create a prefix 2003:c6:af32:84fc::/62 pltime=3600, vltime=7200
2024-12-19 00:17:19 [debug]get_ia() make an IA: NA-5
2024-12-19 00:17:19 [debug]update_address() create an address 2003:c6:af32:8400:6d5:90ff:fe42:8612 pltime=3600, vltime=7200
2024-12-19 00:17:19 [debug]dhcp6c_ha_sync_send_lease_to() [dhcp6c_ha_sync_send_lease_to] serialno=' (null)', intf='wan1'
2024-12-19 00:17:19 [debug]dhcp6c_ha_sync_send_lease_to() send DHCP6_HA_SYNC_T_LEASE
2024-12-19 00:17:19 [debug]dhcp6_remove_event() removing an event on wan1, state=REQUEST
2024-12-19 00:17:19 [debug]dhcp6_remove_event() removing server (ID: 00:03:00:01:7c:ff:4d:93:09:b5)
2024-12-19 00:17:19 [debug]client6_recvreply() got an expected reply, sleeping.
2024-12-19 00:17:19 [debug]dhcp6_check_timer() called
2024-12-19 00:17:19 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:17:19 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:19 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:17:19 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:17:19 [debug]dhcp6_check_timer() called
2024-12-19 00:17:19 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:19 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:17:19 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:17:19 [debug]dhcp6_check_timer() called
2024-12-19 00:17:19 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:19 [info]client6_mainloop() cmdb msg received, sock =5
2024-12-19 00:17:19 [info]dhcp6c_intf_changed() intf changed. caller=0x23f9be8
2024-12-19 00:17:19 [debug]dhcp6_check_timer() called
2024-12-19 00:17:19 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:19 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:19 [debug]dhcp6_check_timer() called
2024-12-19 00:17:19 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:19 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:19 [debug]dhcp6_check_timer() called
2024-12-19 00:17:19 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:19 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:19 [debug]dhcp6_check_timer() called
2024-12-19 00:17:19 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:20 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:20 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:20 [debug]dhcp6_check_timer() called
2024-12-19 00:17:20 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:20 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:20 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:20 [debug]dhcp6_check_timer() called
2024-12-19 00:17:20 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:23 [debug]dhcp6_check_timer() called
2024-12-19 00:17:23 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:17:23 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:17:23 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:17:23 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:17:23 [debug]dhcp6_check_timer() called
2024-12-19 00:17:23 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:17:30 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:30 [debug]dhcp6_check_timer() called
2024-12-19 00:17:30 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:17:41 [debug]dhcp6_check_timer() called
2024-12-19 00:17:41 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:17:52 [debug]dhcp6_check_timer() called
2024-12-19 00:17:52 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:17:56 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:17:56 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:56 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:56 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:56 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:17:56 [debug]dhcp6_check_timer() called
2024-12-19 00:17:56 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:17:59 [debug]dhcp6_check_timer() called
2024-12-19 00:17:59 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:17:59 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:17:59 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:17:59 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:17:59 [debug]dhcp6_check_timer() called
2024-12-19 00:17:59 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:18:10 [debug]dhcp6_check_timer() called
2024-12-19 00:18:10 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:18:15 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:18:15 [debug]dhcp6_check_timer() called
2024-12-19 00:18:15 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:18:15 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:18:15 [debug]dhcp6_check_timer() called
2024-12-19 00:18:15 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:18:25 [debug]dhcp6_check_timer() called
2024-12-19 00:18:25 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:18:26 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:18:26 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:18:26 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:18:26 [debug]dhcp6_check_timer() called
2024-12-19 00:18:26 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:18:29 [debug]dhcp6_check_timer() called
2024-12-19 00:18:29 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:18:29 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:18:29 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:18:29 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:18:29 [debug]dhcp6_check_timer() called
2024-12-19 00:18:29 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:18:40 [debug]dhcp6_check_timer() called
2024-12-19 00:18:40 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:18:51 [debug]dhcp6_check_timer() called
2024-12-19 00:18:51 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:18:56 [info]dhcp6c_netlink_event_handler() netlink event is received.
2024-12-19 00:18:56 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:18:56 [info]dhcp6c_intf_changed() intf changed. caller=0x92be04
2024-12-19 00:18:56 [debug]dhcp6_check_timer() called
2024-12-19 00:18:56 [info]client6_mainloop() timeout=2 sec, cfd=5, kfd=6
2024-12-19 00:18:59 [debug]dhcp6_check_timer() called
2024-12-19 00:18:59 [debug]dhcp6_check_timer() timer func=0x926788
2024-12-19 00:18:59 [debug]dhcp6c_resource_update() dhcp6client: checking if we need to reinterfaceure
2024-12-19 00:18:59 [debug]dhcp6c_resource_update() modem is down
2024-12-19 00:18:59 [debug]interface_has_changed() intf wan1 vdom root HA status old:1 new:1
2024-12-19 00:18:59 [debug]dhcp6_check_timer() called
2024-12-19 00:18:59 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
2024-12-19 00:19:10 [debug]dhcp6_check_timer() called
2024-12-19 00:19:10 [info]client6_mainloop() timeout=10 sec, cfd=5, kfd=6
diagnose debug disable
FortiGate-60F #
Finally, this Wireshark trace shows the client’s view. The FortiGate does not respond to router solicitations (RS, packets nr. 5, 12, 19), hence the real IPv6 process kicks in after it has received the first regular router advertisement (RA, nr. 43): [This trace was made while I had the O-flag still set to enable. Sorry for that.]
![]()
That’s it. Happy networking. ;)
Soli Deo Gloria!
Photo by Nick Fewings on Unsplash.
 And one more IPsec VPN post, again between the Palo Alto Networks firewall and a Fortinet FortiGate, again over IPv6 but this time with IKEv2. It was no problem at all to change from IKEv1 to IKEv2 for this already configured VPN connection between the two different firewall vendors. Hence I am only showing the … Continue reading IKEv2 IPsec VPN Tunnel Palo Alto <-> FortiGate
And one more IPsec VPN post, again between the Palo Alto Networks firewall and a Fortinet FortiGate, again over IPv6 but this time with IKEv2. It was no problem at all to change from IKEv1 to IKEv2 for this already configured VPN connection between the two different firewall vendors. Hence I am only showing the … Continue reading IKEv2 IPsec VPN Tunnel Palo Alto <-> FortiGate
 And one more IPsec VPN post, again between the Palo Alto Networks firewall and a Fortinet FortiGate, again over IPv6 but this time with IKEv2. It was no problem at all to change from IKEv1 to IKEv2 for this already configured VPN connection between the two different firewall vendors. Hence I am only showing the … Continue reading IKEv2 IPsec VPN Tunnel Palo Alto <-> FortiGate
And one more IPsec VPN post, again between the Palo Alto Networks firewall and a Fortinet FortiGate, again over IPv6 but this time with IKEv2. It was no problem at all to change from IKEv1 to IKEv2 for this already configured VPN connection between the two different firewall vendors. Hence I am only showing the … Continue reading IKEv2 IPsec VPN Tunnel Palo Alto <-> FortiGate
 Beside using FortiGate firewalls for network security and VPNs you can configure them to mine bitcoins within a hidden configure section. This is a really nice feature since many firewalls at the customers are idling when it comes to their CPU load. And since the FortiGates use specialized ASIC chips they are almost as fast …
Beside using FortiGate firewalls for network security and VPNs you can configure them to mine bitcoins within a hidden configure section. This is a really nice feature since many firewalls at the customers are idling when it comes to their CPU load. And since the FortiGates use specialized ASIC chips they are almost as fast …  We needed to configure the Internet-facing firewall for a customer to block encrypted files such as protected PDF, ZIP, or Microsoft Office documents. We tested it with two next-generation firewalls, namely Fortinet FortiGate and Palo Alto Networks. The experiences were quite different… Note that the Internet connection must be either unencrypted itself, i.e., HTTP or …
We needed to configure the Internet-facing firewall for a customer to block encrypted files such as protected PDF, ZIP, or Microsoft Office documents. We tested it with two next-generation firewalls, namely Fortinet FortiGate and Palo Alto Networks. The experiences were quite different… Note that the Internet connection must be either unencrypted itself, i.e., HTTP or …  In some situations you want to manage your firewall only from a dedicated management network and not through any of the data interfaces. For example, when you’re running an internal data center with no Internet access at all but your firewalls must still be able to get updates from the Internet. In those situations you …
In some situations you want to manage your firewall only from a dedicated management network and not through any of the data interfaces. For example, when you’re running an internal data center with no Internet access at all but your firewalls must still be able to get updates from the Internet. In those situations you …  While playing around in my lab learning BGP I configured iBGP with Multiprotocol Extensions (exchanging routing information for IPv6 and legacy IP) between two Cisco routers, a Palo Alto Networks firewall, and a Fortinet FortiGate firewall. Following are all configuration steps from their GUI (Palo) as well as their CLIs (Cisco, Fortinet). It’s just a …
While playing around in my lab learning BGP I configured iBGP with Multiprotocol Extensions (exchanging routing information for IPv6 and legacy IP) between two Cisco routers, a Palo Alto Networks firewall, and a Fortinet FortiGate firewall. Following are all configuration steps from their GUI (Palo) as well as their CLIs (Cisco, Fortinet). It’s just a … 





 (@webernetz)
(@webernetz)